41 network security architecture diagram
Network architecture diagrams using UML - overview of ... Network Architecture Diagrams. UML standard has no separate kind of diagrams to describe network architecture and provides no specific elements related to the networking.Deployment diagrams could be used for this purpose usually with some extra networking stereotypes.Network architecture diagram will usually show networking nodes and communication paths between them. Azure network architecture | Microsoft Docs The Azure network architecture provides connectivity from the Internet to the Azure datacenters. Any workload deployed (IaaS, PaaS, and SaaS) on Azure is leveraging the Azure datacenter network. Network topology. The network architecture of an Azure datacenter consists of the following components: Edge network; Wide area network; Regional ...
What Is Network Architecture? Types of Network Architecture What Is a Network Architecture Diagram? A Network Architecture Diagram is the visual representation of the network. The layout of the elements that constitute a network is represented with various symbols and lines. Visual representation is the most intuitive way to process information and understand how network elements are connected.
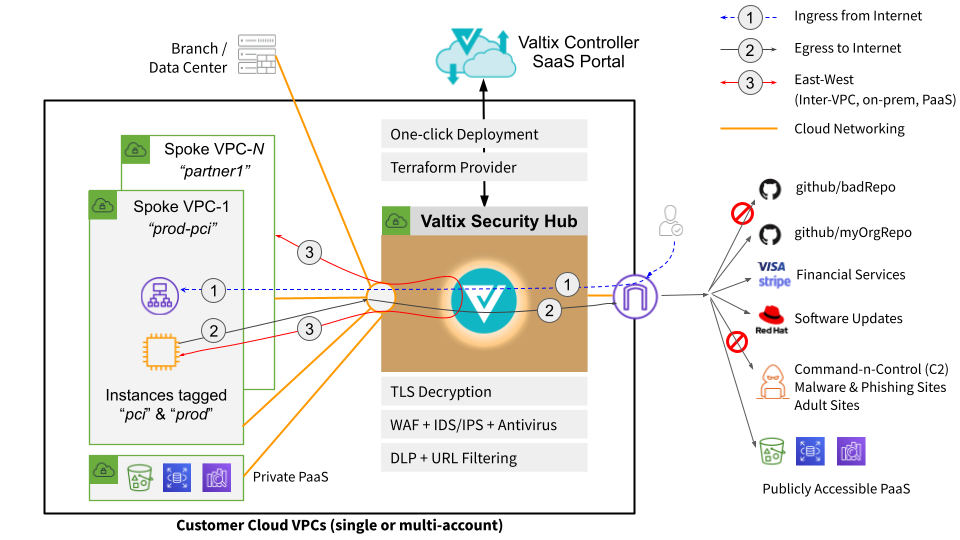
Network security architecture diagram
Nist Network Security Architecture Diagram - 19 images ... [Nist Network Security Architecture Diagram] - 19 images - ppt rda big data infrastructure wg powerpoint, the cybersecurity framework temporal based intelligence, nist csf core notes cyber security memo, network architecture left protocol stack middle and, Elements to a Great Network Diagram | RSI Security Network Security Measures Firewalls and authentication tools also form part of the network architecture diagram. These components identify access points and remedial response measures in the event of a breach or malicious intrusion. Web Service or Presence All client-facing digital tools represent additional attack vectors. Network Security Architecture Diagram | Enterprise ... Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices. You dream to find powerful software for easy designing Network Security Architecture Diagram?
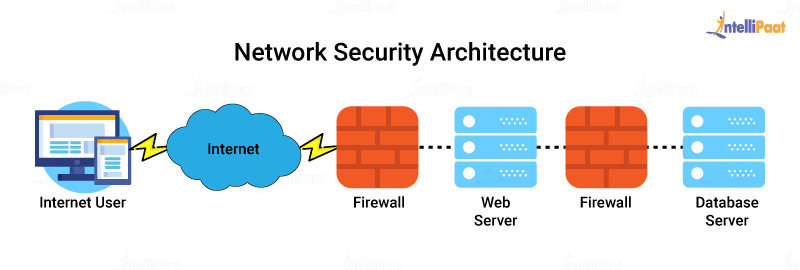
Network security architecture diagram. Cybersecurity Architecture, Part 2: System Boundary and ... In this post, we presented an outside-in approach to security architecture reviews that has worked for us, starting with two focus areas, System Boundary and Boundary Protection. In Part 3 of our Cybersecurity Architecture series, we'll discuss three more focus areas: Asset Management, Network Segmentation, and Configuration Management. What is a Network Diagram | Lucidchart The Ultimate Network Diagram Guide - Understand the history of network diagrams and learn about common symbols. See examples and learn how to make a network diagram from scratch. Customize a network diagram template or create your own … Network security strategies on Azure - Microsoft Azure ... Segment your network footprint and create secure communication paths between segments. Align the network segmentation with overall enterprise segmentation strategy. Design security controls that identify and allow or deny traffic, access requests, and application communication between segments. Protect all public endpoints with Azure Front Door ... Network Topology, Architecture, and Segmentation Diagrams ... A network architecture diagram, also known as a network infrastructure diagram, helps admins visualize their complete network infrastructure and architecture. It provides a comprehensive picture of resources and network layers, potentially including hardware, layout and topology, wireless connections, software, protocols, and more.
PDF NIST Cloud Computing Security Reference Architecture 1 1 . NIST Special Publication 500-299 . 2 . 3 . 4 . 5 . NIST Cloud Computing 6 . Security Reference Architecture 7 . 8 . 9 . 10 . 11 . 12 . NIST Cloud Computing ... Network Diagrams: Key to Compliance and Security If you were to ask network architects and engineers about their favorite part of the job, I doubt any of them will respond with "creating and maintaining network diagrams." It's not the most glamorous task—yet requirements 1.1.2 and 1.1.3 of the Payment Card Industry Data Security Standard (PCI DSS), along with general good security hygiene, render it a necessary one. PDF Chapter 6 - Domain 5: Security architecture and design Network Security) is an example of network layering. Unlike the OSI model, the layers of security architecture do not have standard names that are universal across all architectures. A generic list of security architecture layers is as follows: 1. Hardware 2. Kernel and device drivers 3. Operating System 4. Applications In our previous IDE ! Microsoft Cybersecurity Reference Architectures - Security ... The reference architectures are primarily composed of detailed technical diagrams on Microsoft cybersecurity capabilities, zero trust user access, security operations, operational technology (OT), multi-cloud and cross-platform capabilities, attack chain coverage, azure native security controls, and security organizational functions.
The Importance of having a Network Diagram | RSI Security Vital Role of Network Architecture Diagram When it comes to troubleshooting network configurations, a network architecture diagram removes the guesswork out of the equation. It saves resources such as money and time when it comes to restarting a network. PDF Federal Enterprise Architecture - NIST NI -1 Network Connectivity Diagram C3/R5 NI -2 Network Inventory C3/R5 NI -3 Capital Equipment Inventory C3/R5 NI -4 Building Blueprints * C3/R5 NI -5 Network Center Diagram C3/R5 NI -6 Cable Plant Diagram C3/R5 NI -7 Rack Elevation Diagram C3/R5 Security (SP) Cybersecurity Reference Architecture: Security for a ... The Microsoft Cybersecurity Reference Architecture describes Microsoft's cybersecurity capabilities and how they integrate with existing security architectures and capabilities. We recently updated this diagram and wanted to share a little bit about the changes and the document itself to help you better utilize it. Network Security Architecture Diagram - ConceptDraw network security architecture diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices, such as firewalls, antivirus programs, network monitoring tools, tools of detecting attempts of unauthorized …
Security Architecture | Components of Security Architecture Security architecture is a type of enterprise architecture and is very important for the organization to protect the company resources from the outside world. A strong security architecture is used by the organization to main security and data integrity in the system, and the policies and rules defined by the system are followed by the employee ...
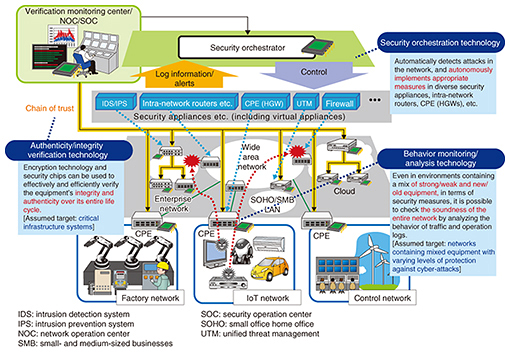
PDF Network Security Reference Architecture - Fortinet Network Security Components and Reference Architectures Subject This document contains components critical for network security and provides a number of use cases and architectures for Intent Based Segmentation which aligns business goals with what is achievable on the network.
PDF IT SECURITY ARCHITECTURE - Energy The DOE IT Security Architecture approaches IT Security as a distinct set of business activities ... routinely flows in and out of a network through . IT Security Architecture February 2007 6 numerous access points. This separation of information from systems requires that the
Network Security Architecture Diagram | Cyber Security ... Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices. You dream to find powerful software for easy designing Network Security Architecture Diagram?
Network Security Architecture - SlideShare Application level security such as Active Directory trust levels should be closely aligned to the network architecture. - No trust levels should be implied because network traffic is either allowed or denied Specific principles Traffic from the untrusted zone (0) to the trusted or restricted zone (100) shall be specifically denied.
Network Security Architecture Diagram | How to Draw a ... Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices. You dream to find powerful software for easy designing Network Security Architecture Diagram?
Network Security Diagram Template - Visual Paradigm Network Security Diagram Template. Edit this Template. Edit Localized Version: 網絡安全圖模板 (TW) | 网络安全图模板 (CN) View this page in: EN TW CN. Draw Network Diagram with Visual Paradigm Online (VP Online), a web-based Network Diagram maker. The Network Diagram editor has tailor-designed features that ease the editing of chart.
Network Security Groups - docs.oracle.com Network security groups (NSGs) act as a virtual firewall for your compute instances and other kinds of resources.An NSG consists of a set of ingress and egress security rules that apply only to a set of VNICs of your choice in a single VCN (for example: all the compute instances that act as web servers in the web tier of a multi-tier application in your VCN).
Network Security Architecture Diagram | Cyber Security ... Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices. You dream to find powerful software for easy designing Network Security Architecture Diagram?
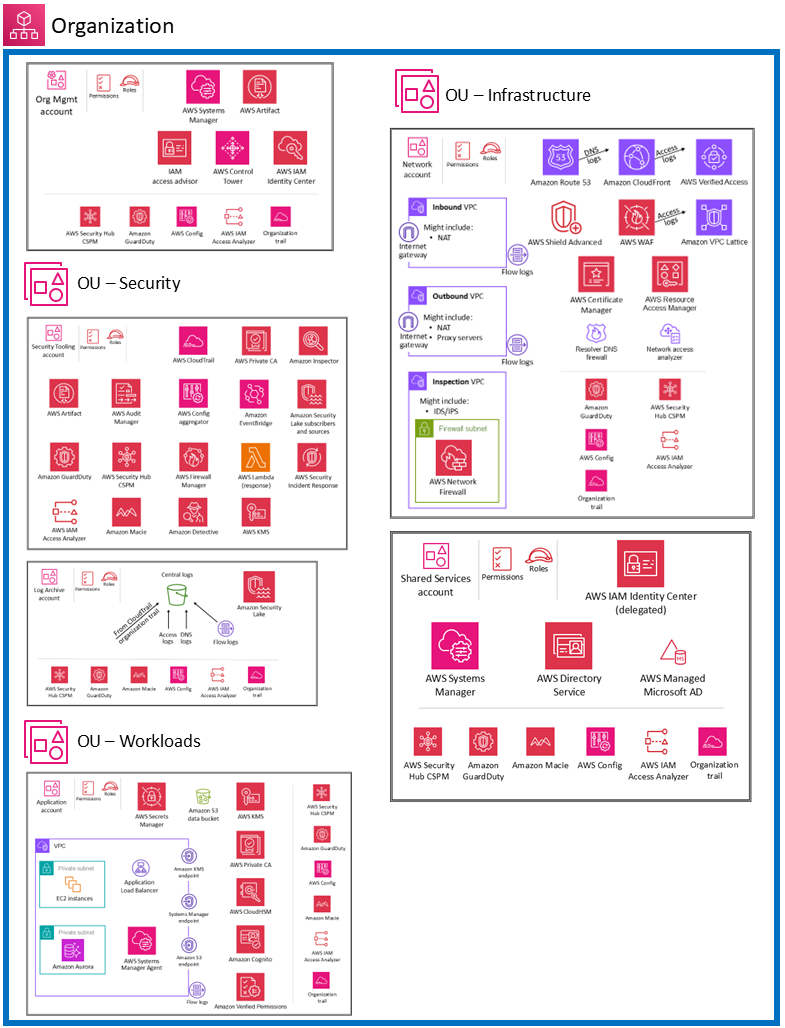
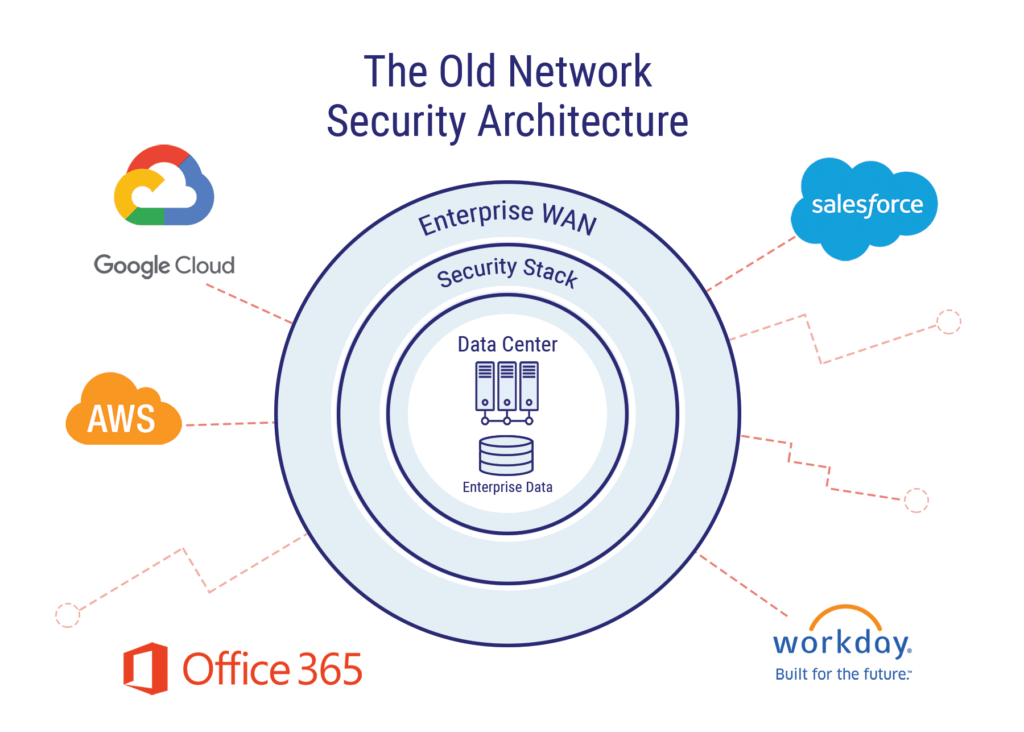
The AWS Security Reference Architecture - AWS Prescriptive ... Most architecture diagrams focus and dive deep on the web, application, and data tiers. For readability, they often omit the security controls. This diagram flips that emphasis to show security wherever possible, and keeps the application and data tiers as simple as necessary to show security features meaningfully.
PDF Security Architecture - Cisco Cisco's Network Security Architecture Borderless Data Center 3 Borderless Internet 2 Borderless End Zones 1 Policy Corporate Border Branch Office Applications and Data Corporate Office Policy 4 (Access Control, Acceptable Use, Malware, Data Security) Home Office Attackers Coffee Customers Shop Airport Mobile User Partners
Bank Security Architecture [classic] | Creately Bank Security Architecture [classic] Use Creately's easy online diagram editor to edit this diagram, collaborate with others and export results to multiple image formats. You can edit this template and create your own diagram. Creately diagrams can be exported and added to Word, PPT (powerpoint), Excel, Visio or any other document.
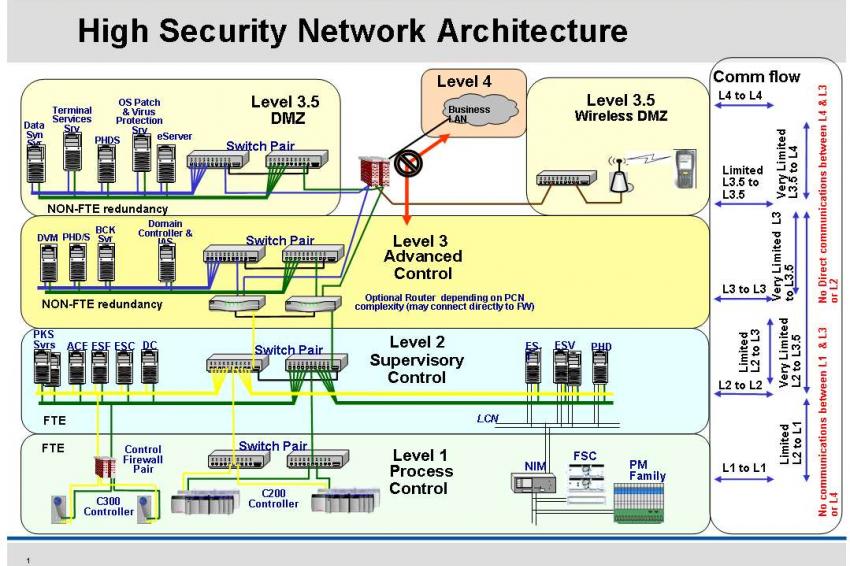
The Ultra-Secure Network Architecture - RSM US The Ultra-Secure Network Architecture The diagram below represents the base-level ultra-secure network architecture, which meets all regulatory requirements and limits the likelihood of information being obtained as long as all of the architectural components are properly managed, maintained and monitored.
Network Security Architecture Diagram | Enterprise ... Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices. You dream to find powerful software for easy designing Network Security Architecture Diagram?
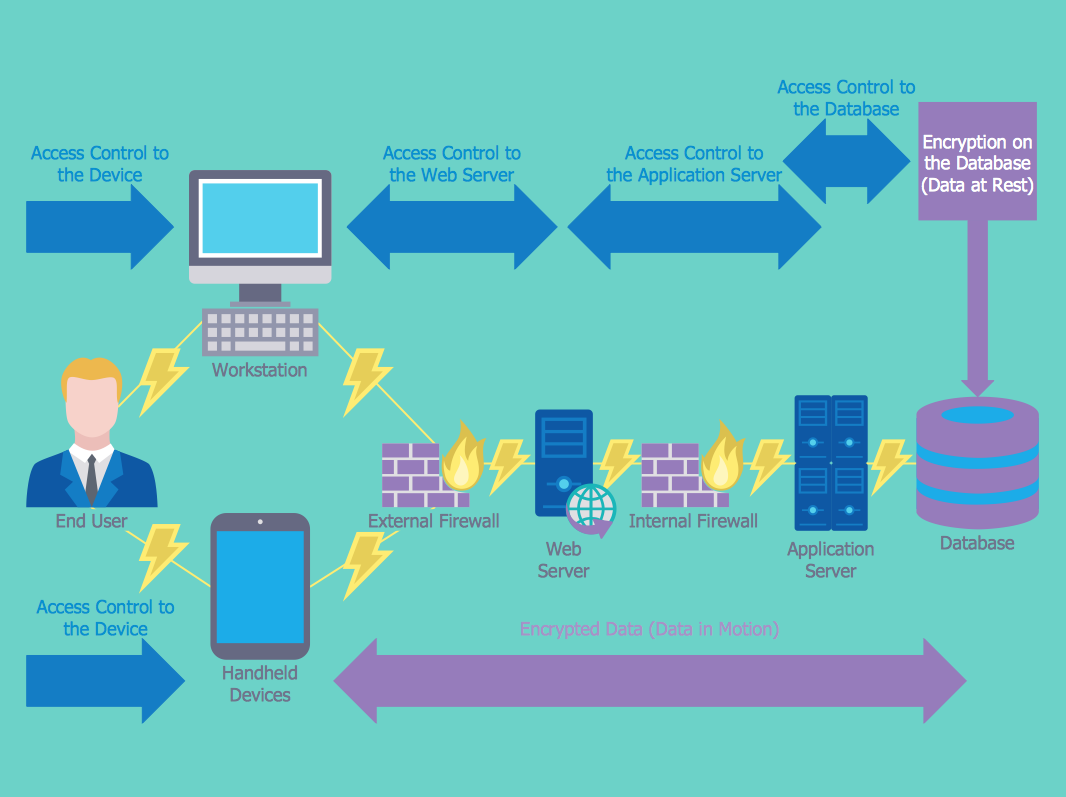
Elements to a Great Network Diagram | RSI Security Network Security Measures Firewalls and authentication tools also form part of the network architecture diagram. These components identify access points and remedial response measures in the event of a breach or malicious intrusion. Web Service or Presence All client-facing digital tools represent additional attack vectors.
Nist Network Security Architecture Diagram - 19 images ... [Nist Network Security Architecture Diagram] - 19 images - ppt rda big data infrastructure wg powerpoint, the cybersecurity framework temporal based intelligence, nist csf core notes cyber security memo, network architecture left protocol stack middle and,
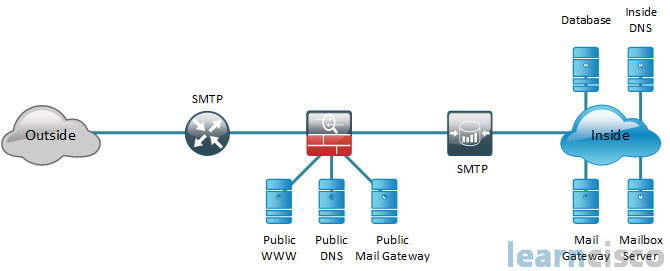
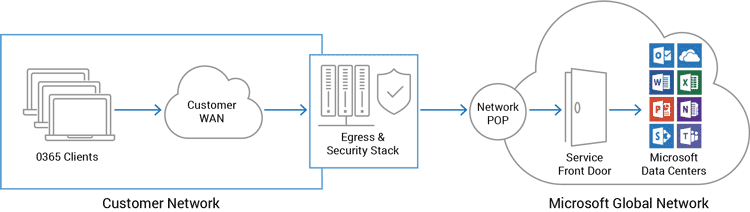
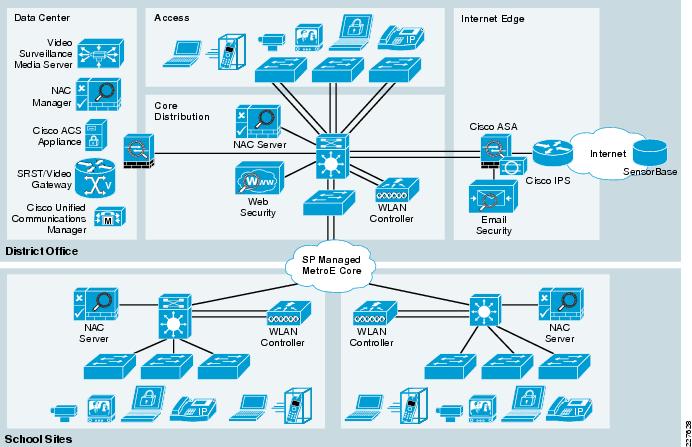

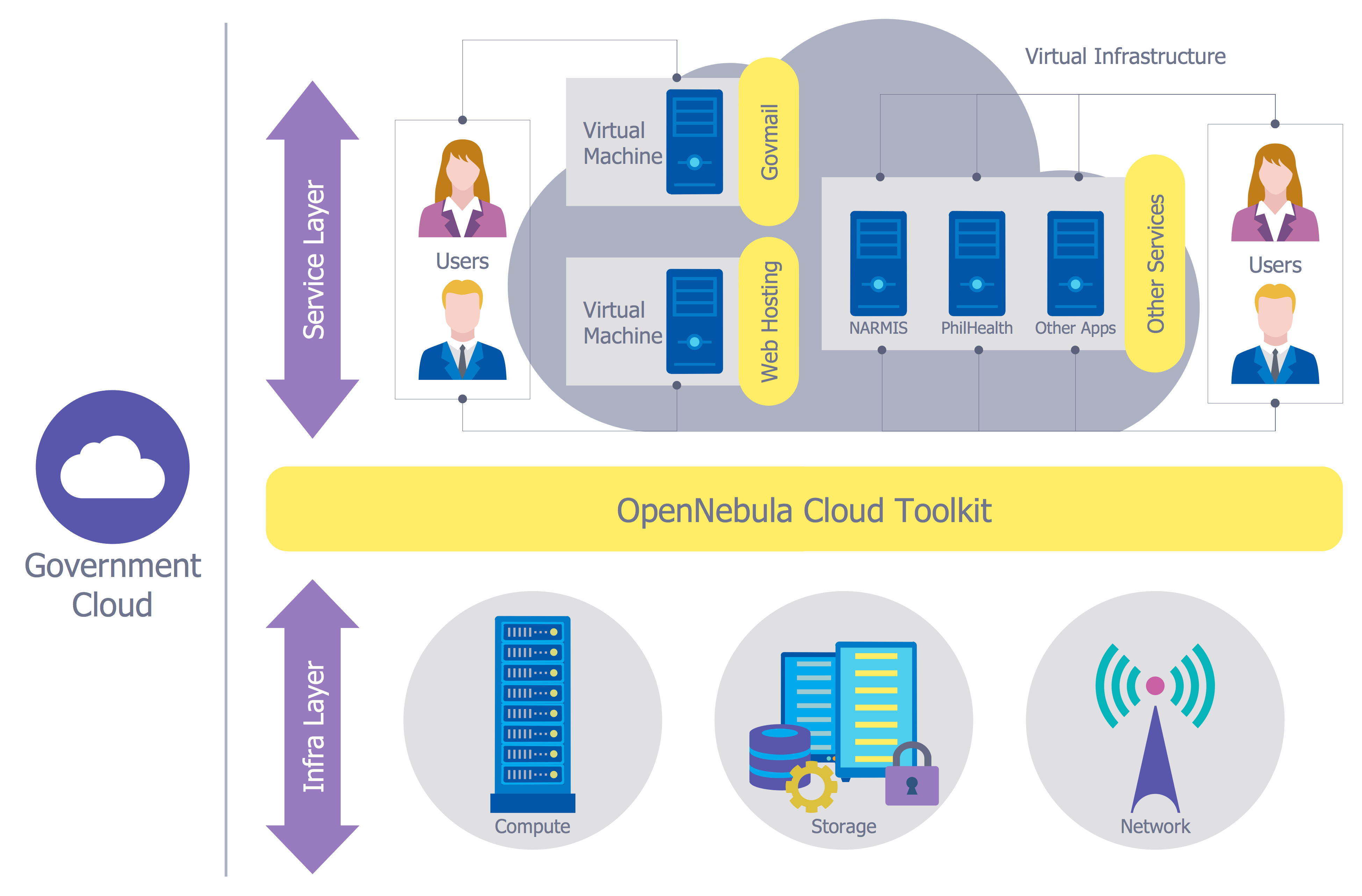
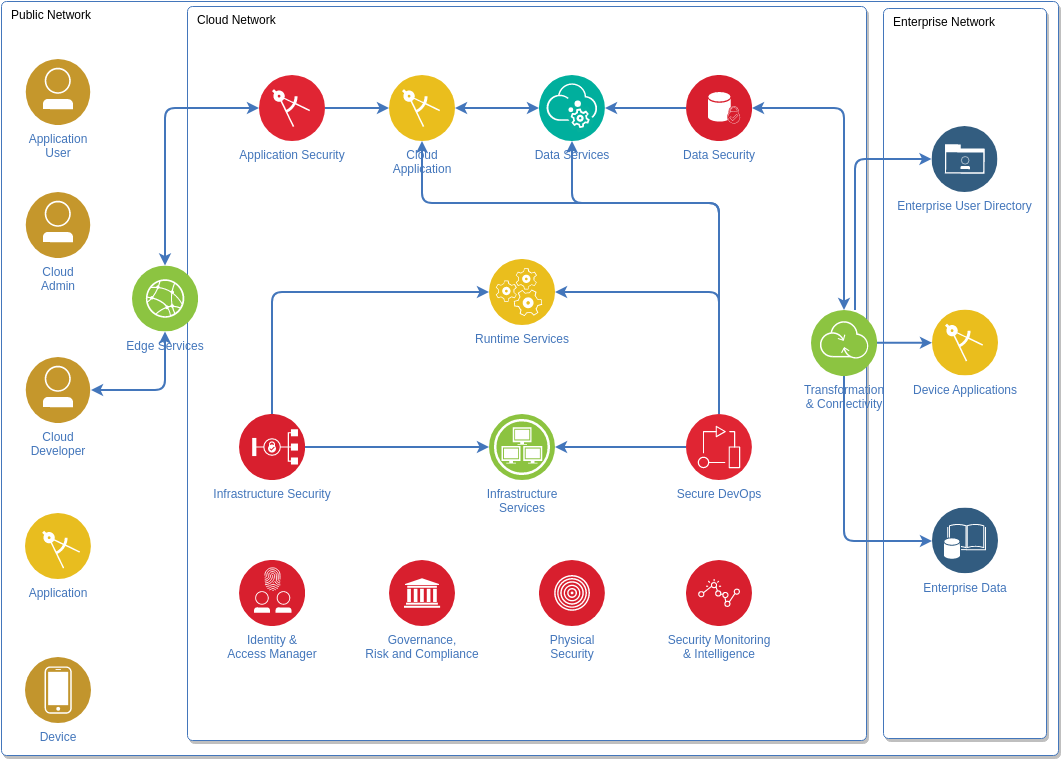
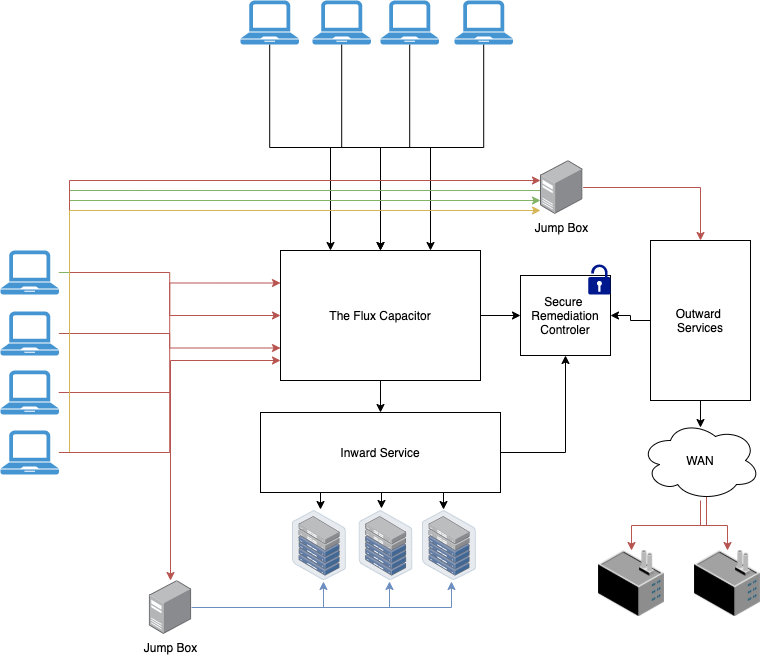
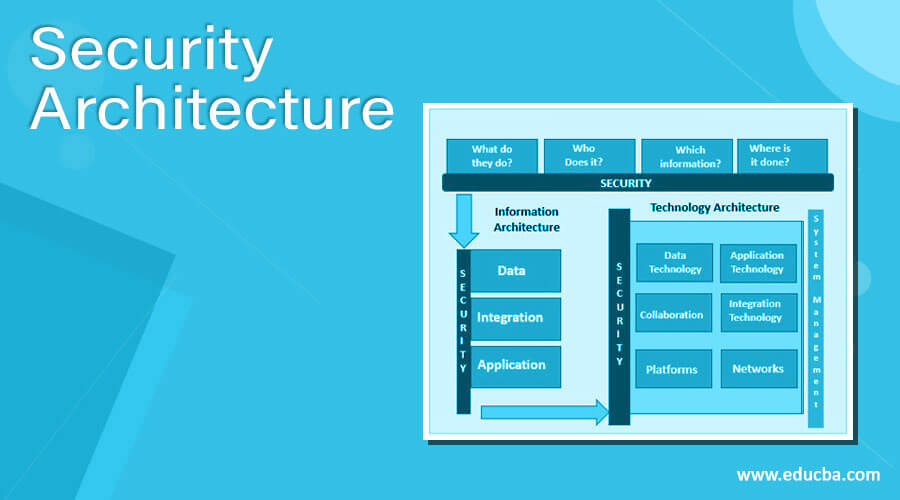



![PDF] The Global Voice of Information Security Network ...](https://d3i71xaburhd42.cloudfront.net/5756859705f57cfdf799fd2f790f5b7b0ccf334a/3-Figure2-1.png)













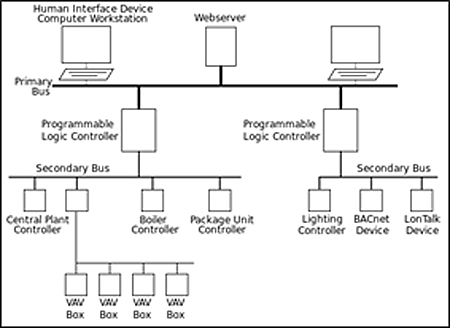
0 Response to "41 network security architecture diagram"
Post a Comment